BLOG
Assessing your security landscape
Remote working is not new, but the scale of remote working has shifted enormously. As such, the risk profile attached to our remote colleagues changes, and the focus that we need to put on securing the technologies used by our colleagues increases. I am often asked about what are the first things I consider when assessing a business’ security portfolio, so I thought I would share some of my process with you in this blog.
If we look at 2019 Cyber Security insights, specifically breaches within the UK, we can see a number of areas of concern that will inform assessment of your portfolio. According to the Cyber Breach report by the Department of Culture, Media and Sport the key areas that triggered breaches were:
- Phishing attacks (affecting 80% of all surveyed companies)
- Others impersonating an organisation online or via email (28% of all surveyed companies)
- Viruses, spyware and malware (27% of all surveyed companies)
This information clearly shows that the biggest and most successful attack vector for cyber criminals is the end user.

COVID-19 content is now also being used to lure unsuspecting users, and the need to protect our colleagues, customers and our businesses is even greater. Click here for our useful paper on some of the COVID-19 scams you should be aware of and what to look for.
No doubt that there has been some changes to the way in which businesses operate, but whether you’re a cloud-only business, or you have increased VPN and VDI capacity, I hope that there will be something within this blog and the associated whitepaper that is useful to you.
The first area I talk to my customers about is using a ‘Zero Trust Model.’ This isn’t a technology, it’s an approach to security that guides technology and processes in the quest for better security. The Zero Trust model is gaining significant traction in the marketplace and it’s a model I am an advocate for. Security experts see this as one of the best models for reducing the number of cyber breaches. The concept is simple at its roots: do not automatically trust anything; inside or outside your organization, without first verifying it before granting access. No networks, no devices and no users.
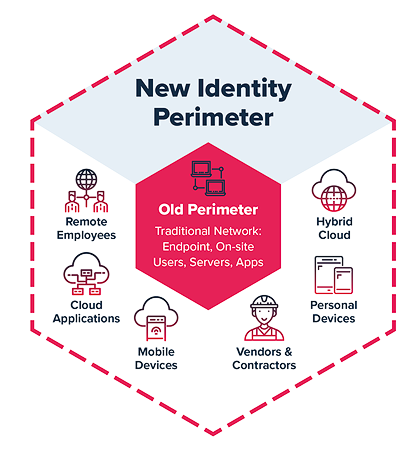 This approach does away with the old model of securing your perimeter and controlling everything within it, assuming everyone inside doesn’t pose a threat. So we start from the inside out, securing what’s inside the organization, and working our way out instead.
This approach does away with the old model of securing your perimeter and controlling everything within it, assuming everyone inside doesn’t pose a threat. So we start from the inside out, securing what’s inside the organization, and working our way out instead.
Starting from the inside out, these are the areas that that I would recommend looking at first when assessing the cyber security across your business security landscape:
- Incident Response
- SIEM, SOC and Automation
- Email Security
- Web security
- Identity and Access Management
- BYOD
- Cloud security
- Data Protection and DR
- Endpoint protection and response; and
- Overall security awareness and knowledge for end users
For those who would like more information about the areas above, I have created this whitepaper that explores each of these security areas in more detail.

I am aware that I have listed a lot of considerations that could undermine some of the principles of looking for simplicity and protection. For this reason I suggest having a reputable and reliable security partner that you trust, who can truly understand your business landscape, your desired level of protection, and work within your budget to achieve this. If you want to do it yourself and have the skills in-house to do so, I suggest that when evaluating new tools, consider tools that share intelligence, work together or sit under the same ecosystem to provide a singular view. Getting technology that works together is by far the best way to close the gap on detection and response.
If you would like to discuss any of the above principles in more detail or debate any of my advice, I welcome you to please get in touch.
Sources:

Timico
We deliver Connectivity, UC&C, Cloud & Hosting, Security and IT Managed Service Solutions to our customers, through Service Operations based in Newark, Winnersh, Telford and London.